When I was a kid, my father always used to apprise me that, “Son, God is everywhere. He is watching all your activities”. But I used to think that how’s that possible. Thankfully, now I got to know what it meant actually.
The Pegasus spyware is a surveillance software, developed by NSO Group, an Israeli cyber arms firm, that can be surreptitiously installed on mobile and other technological devices running most versions of Android or iOS. Pegasus effect on the phone is instinctively capable of reading and gathering all important information stored in our electronic gadgets by way of reading text messages, passwords, tracking, camera, microphone, and manufacturing information from apps.
NSO Group is known to build sophisticated software and technology for selling solely to law enforcement and intelligence agencies of vetted governments for the sole purpose of risk management in cybersecurity to prevent crime and terror acts, as claimed by the company. The spyware is named after a fictional winged horse character named, Pegasus and is a Trojan Horse that can fly high to keep our mobile data in its way.
Initially, Pegasus spyware started initiating headlines in the year 2016 when it was outbursted that there was an unsuccessful attempt of an attack on the device of UAE human rights activist Ahmed Mansoor. He had received text messages on his iPhone providing ‘new secrets’ about tortured prisoners in the country if he opened a link in the SMS. Instead of following the instructions, Mansoor sent the messages to the researchers at Citizen Lab, who tracked the origin of the links back to the infrastructure belonging to NSO Group. It was revealed that the link gave access to the Pegasus spyware that could exploit vulnerabilities in an iOS and infect it by giving unlimited access to the data on the device.
Then, WhatsApp in 2019 had released a statement agreeing that a cyberattack by spyware exploited their software’s vulnerabilities and has infected roughly 1,400 devices across 20 countries widening four continents. The attack targeted several activists, lawyers, and journalists and of which 20 were Indians. It was allegedly carried out using the Israel-based NSO Group’s spyware, Pegasus, which allowed the surveillance to be conducted on individuals via their electronic devices and smartphones.
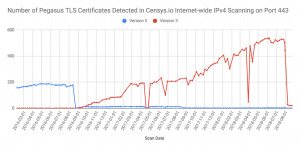
Source: The Citizen Lab
The image above shows the number of Pegasus TLS Certificates detected.
In the early days, one of the main vulnerable schemes was via SMS. The victim got an SMS with a link. If the person clicks on it then their device gets infected with the spyware.
But the Pegasus spyware has a unique capability of launching network injection attacks on user’s devices that are initiated remotely, i.e, without the target’s engagement. It is also referred to as zero-click engagement as the spyware gets engaged with a device without any clicks which can be mainly through missed calls. This also gave NSO group flagship product an edge over other spyware. It is also known by names, Q suite, and Trident.
The Organized Crime and Corruption Reporting Project (OCCRP) report says that as the public became more aware of these tactics and was effectively able to deal with malicious spam, zero-click exploitation was revived. Zero-click relies on bugs in very popular apps like WhatsApp, which sometimes receive and transmit data from unknown sources. If any vulnerability is found, Pegasus can infiltrate a device using the IP address of the app. The user does not have to access a link, read a message, or even answer a call.
OCCRP also reported another method called “network injections” to quietly access a target’s device. A Web browser can leave an individual vulnerable to attack without the need for them to click on a specifically designed malicious link. This approach involves waiting for the target to visit a website that is not secured during their normal activity. Once they click on a link to the site, the NSO Group’s software access the phone and transmits an infection.
The software can also copy an application uploaded to an iPhone and transmit itself as push notifications via Apple’s servers. Thousands of iPhone handsets have been potentially restricted by the NSO spyware.
Pegasus for Android does not rely on zero-day vulnerabilities and thus, uses a rooting method called Framaroot. Framaroot is an application, capable of rooting Android devices without the need of a computer or any other sources. Also, if the iOS version fails to bunk the device, the whole attack fails. This is not the case with the Android version as when the malware fails to obtain the necessary root access to install surveillance software, it still tries indirectly asking the user for the permissions it needs to abjure some data.
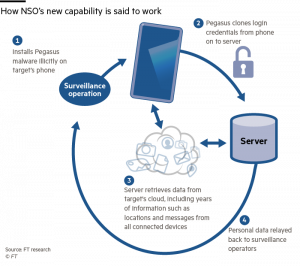
Source: FT Research
The image above scrutinizes the process of infiltration by the spyware.
There Is A Way To Every Problem
While the antivirus apps can help protect the mobile phone from malware but they cannot follow its Pegasus spyware. Also, it can easily port to nearby networking devices and run for information, and thus, switching off the internet will only slow them down. According to the latest reports, Pegasus can carry out chip-level attacks. These attacks remain on the phone even after a factory reset.
Although it’s very cumbersome and unfathomable to discover solutions by remitting the spyware, some solutions for data breach management are effective enough to protect an individual from this contagious ransomware.
- Get your devices updated on time and allow special attention to security updates.
- Get installed a good security solution on your device. There are none for iOS, but Pegasus will make Apple rethink its policy.
- Last, but not least is, don’t fall for phishing, even if it’s targeted bull’s eye spear phishing. If a link from an unknown source is received, prohibit yourself to not click on it. There’s, a saying, “Think before you speak” but the policy to follow for this spyware is, “Think before you Click”.
Encryption helps when the phone has been taken out and is broken, but Pegasus stays. The spyware can gather screenshots of whatever you are doing and send them to the operators.
Conclusion: Technology is Magic
Now, Pegasus is in the middle of a Global Collaborative Investigative Project that has found that the spyware used to target hundreds of mobile phones in India.
Through Pegasus, corrupt and bureaucratic regimes across the world can pocket access to tremendous tides of personal information. The spyware goal was to be sold as a crime-fighting tool but it is already known to have been used against journalists, activists, and political dissidents.
A group of journalists in India gained access to a list of 50,000 phone numbers that had allegedly been picked as targets of the spyware. It is worth noting that Pegasus is a complex and expensive malware, designed solely to spy on individuals and institutions of particular interest, so the average user is unlikely to portend it. Pegasus has been a new introductory session to our lives and is a nightmare for many innocents. Therefore, pegasus risk management should be undertaken, otherwise, it might take many nations to nadir.
In my childhood, Pegasus was a different meaning to me. I thought it to be real but later reasoned it as fiction. My childhood was a great journey where characters were fictional, but now it’s a reality that has moved away from a fictional love for a character in my heart.
- https://www.google.com/url?sa=t&source=web&rct=j&url=https://www.forbes.com/sites/kateoflahertyuk/2021/07/25/pegasus-spyware-this-new-app-says-it-can-instantly-check-for-pegasus/amp/&ved=2ahUKEwj0xemjqpDyAhXDUn0KHWWtBEIQFjAPegQICxAC&usg=AOvVaw01zk-IHvkxW9xgrEOTIE6g&cf=1&cshid=1627838942431
- https://m.economictimes.com/news/india/does-anti-virus-encryption-solutions-help-against-pegasus-like-hacking/what-if-i-switch-off-my-mobile-data-or-wifi/slideshow/84609219.cms
- https://www.google.com/url?sa=t&source=web&rct=j&url=https://amp.theguardian.com/news/2021/jul/18/what-is-pegasus-spyware-and-how-does-it-hack-phones&ved=2ahUKEwj0xemjqpDy
- hXDUn0KHWWtBEIQFjALegQIFRAC&usg=AOvVaw3WSv0Ge3L26C2LAtOS1IUG&cf=1&cshid=1627838942431Blog Published By: Vaibhav Aggarwal, Student Risk Committee Member